此工具是一款非常好用的Windows下提权辅助工具(已经支持Windows 10下的提权了),国内已经有许多人在用了,但是一直没有相应的中文文档,所以我特地翻译了一下,水平有限,如有错误,欢迎指出,谢谢。
描述
该工具可以将目标系统的补丁安装情况与微软的漏洞数据库进行对比,进而检测出目标系统中潜在的未修复漏洞。同时此工具还会告知用户针对于此漏洞是否有公开的exp和可用的Metasploit模块。
同时它可以使用–update参数去自动化地从微软下载漏洞补丁数据库,并将其以Excel表格的形式保存。
需要注意的是,此工具首先会假定目标系统存在所有漏洞,然后再基于系统补丁情况去选择性的移除已修补漏洞。故此工具可能会造成一些误报,因此你首先需要了解目标机器安装了哪些软件。例如,如果此机器没有IIS的补丁,即使机器上没有IIS,工具也同样会认为存在此漏洞。
此工具很大程度上受了Pentura的Linux_Exploit_Suggester的启发。
使用方法
1.首先需要更新漏洞数据库
$ ./windows-exploit-suggester.py --update
[*] initiating...
[*] successfully requested base url
[*] scraped ms download url
[+] writing to file 2014-06-06-mssb.xlsx
[*] done2.然后安装程序依赖:python-xlrd
watcher@ubuntu:~/xlrd-0.9.4/xlrd-0.9.4$ sudo python setup.py install
[sudo] password for watcher:
running install
running build
running build_py
running build_scripts
running install_lib
creating /usr/local/lib/python2.7/dist-packages/xlrd
copying build/lib.linux-x86_64-2.7/xlrd/compdoc.py -> /usr/local/lib/python2.7/dist-packages/xlrd
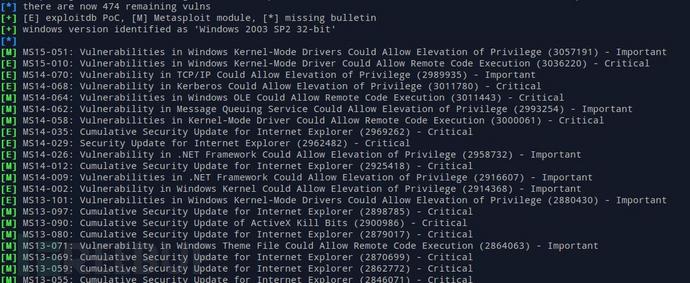
......3.接着在目标机器中执行systeminfo,并将其输出到文件中,然而带入参数–systeminfo中,并指定数据库位置(就是那个excel文件)
$ ./windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --systeminfo win7sp1-systeminfo.txt
[*] initiating...
[*] database file detected as xls or xlsx based on extension
[*] reading from the systeminfo input file
[*] querying database file for potential vulnerabilities
[*] comparing the 15 hotfix(es) against the 173 potential bulletins(s)
[*] there are now 168 remaining vulns
[+] windows version identified as 'Windows 7 SP1 32-bit'
[*]
[M] MS14-012: Cumulative Security Update for Internet Explorer (2925418) - Critical
[E] MS13-101: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2880430) - Important
[M] MS13-090: Cumulative Security Update of ActiveX Kill Bits (2900986) - Critical
[M] MS13-080: Cumulative Security Update for Internet Explorer (2879017) - Critical
[M] MS13-069: Cumulative Security Update for Internet Explorer (2870699) - Critical
[M] MS13-059: Cumulative Security Update for Internet Explorer (2862772) - Critical
[M] MS13-055: Cumulative Security Update for Internet Explorer (2846071) - Critical
[M] MS13-053: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2850851) - Critical
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[*] done下面这条指令可以列出指定操作系统版本存在的所有可能EXP(假设目标系统没有打任何补丁)
$ ./windows-exploit-suggester.py --database 2014-06-06-mssb.xlsx --ostext 'windows server 2008 r2'
[*] initiating...
[*] database file detected as xls or xlsx based on extension
[*] getting OS information from command line text
[*] querying database file for potential vulnerabilities
[*] comparing the 0 hotfix(es) against the 196 potential bulletins(s)
[*] there are now 196 remaining vulns
[+] windows version identified as 'Windows 2008 R2 64-bit'
[*]
[M] MS13-009: Cumulative Security Update for Internet Explorer (2792100) - Critical
[M] MS13-005: Vulnerability in Windows Kernel-Mode Driver Could Allow Elevation of Privilege (2778930) - Important
[E] MS11-011: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (2393802) - Important
[M] MS10-073: Vulnerabilities in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (981957) - Important
[M] MS10-061: Vulnerability in Print Spooler Service Could Allow Remote Code Execution (2347290) - Critical
[E] MS10-059: Vulnerabilities in the Tracing Feature for Services Could Allow Elevation of Privilege (982799) - Important
[E] MS10-047: Vulnerabilities in Windows Kernel Could Allow Elevation of Privilege (981852) - Important
[M] MS10-002: Cumulative Security Update for Internet Explorer (978207) - Critical
[M] MS09-072: Cumulative Security Update for Internet Explorer (976325) - Critical许可
本程序为自由软件;您可依据自由软件基金会所发表的GNU 通用公共授权条款,对本程序再次发布和/ 或修改;无论您依据的是本授权的第三版,或(您可选的)任一日后发行的版本。
本程序是基于使用目的而加以发布,然而不负任何担保责任;亦无对适售性或特定目的适用性所为的默示性担保。详情请参照GNU 通用公共授权。
您应已收到附随于本程序的GNU 通用公共授权的副本;如果没有,请参照<http://www.gnu.org/licenses/>.
*参考来源:github、gdssecurity,watcher编译,转载请注明来自FreeBuff黑客与极客(FreeBuf.COM)
-
 周鸿祎我大360马上杀残它
周鸿祎我大360马上杀残它 -
 Z@ hi 你觉得server上装python的概率有多大?
Z@ hi 你觉得server上装python的概率有多大? -
我来补下工具的下载地址吧:https://github.com/GDSSecurity/Windows-Exploit-Suggester/
-
 by小音这看上去不只是一个提权的辅助工具吧?
by小音这看上去不只是一个提权的辅助工具吧? -
 hi@ XXXX 这些exp metasploit基本都有啊,有0day的毕竟是少数人啊
hi@ XXXX 这些exp metasploit基本都有啊,有0day的毕竟是少数人啊
不容错过
- 外媒报道:中国知名ARM制造商全志科技在Linux中留下内核后门dawner2016-05-13
- 翻墙?隐私?今天聊聊VPN的那些事儿dawner2016-06-12
- Splunk+蜜罐+防火墙=简易WAFRipZ2016-12-05
- “鑫胖”家的红星3.0系统被曝漏洞,可远程执行任意命令注入bimeover2016-12-07
0daybank

 关注我们 分享每日精选文章
关注我们 分享每日精选文章




已有 20 条评论
niubi
@ 周鸿祎 66666666
我大360马上杀残它
我来补下工具的下载地址吧:https://github.com/GDSSecurity/Windows-Exploit-Suggester/
前提是这些EXP你都有,如果这些EXP你都有,那有一两个0DAY也再正常不过了,直接打就是了,要这个干鸟?
@ XXXX 这些exp metasploit基本都有啊,有0day的毕竟是少数人啊
@ hi 你觉得server上装python的概率有多大?
@ Z 这个是运行于自己的机器啊
@ hi 这个是在本地查询的 你是不是两脸懵逼了
@ guanji 在目标机器导出systeminfo信息,将其下载到本机进行漏洞匹配,呵呵,垃圾,你能不能看我再说,太垃圾了你小白
这看上去不只是一个提权的辅助工具吧?
感谢分享出来做实战杠杠的 。
谢谢分享
mark,谢谢分享
就问我服务器上是不是要装个Python 让你提权,给你方便
@ LandGrey 这个是运行于本机的,谢谢,耐心看完文章,别那么浮躁
擦擦擦
很棒,mark一下
谢谢分享
现在的人看不完文章就开始喷,太浮躁了,好东西,谢谢分享1